What is ransomware?
Ransomware is a type of malicious virus that blocks your access to your own files or will threaten to distribute this information unless a ransom is paid. More advanced versions use cryptoviral extortion which will encrypt the user’s data and a ransom must be paid in order to unencrypt the information.
In May 2017 the extremely high-profile “WannaCry Worm” was a Ransomware deployed which targeted Microsoft Windows OS and was able to travel between user computers without any interaction between users. The cryptovirus demanded payment in Bitcoin currency.
Even though Microsoft released a patch for this vulnerability near the time of the attack, most users affected were still operating under older versions of Windows OS or computers that had reached their EOL (end of life) which still contained the vulnerability and had not kept their software updated to the most current version.
While Windows managed to patch the issue within a few days of its discovery and prevent further spread, the damage was said to have affected over 200,000 computers in 150 countries. Costs were estimated to be in the hundreds of millions, if not billion dollar range.
How do I protect myself from ransomware?
Ransomware often presents itself in the form of a Trojan Horse, which if you aren’t aware of the obvious signs would seem like an unexpected (or sometimes expected) email from a well-known company or familiar email.
Below are practices to employ to prevent yourself from becomming the next ransomware victim:
Use a reliable spam-filtering software
Spam filtering can take a lot of the load off of your inbox and dramatically reduce the risk of malicious threats making their way into company inboxes. We can offer a few different solutions for spam filtering and security education for your business. Learn more about secure email services here, or contact us today.
When in doubt, don’t click
If an email or file looks suspicious in any way, do not open it, and do not click on any embedded links within them. Analyze the link before clicking; in most email programs you can simply hover your cursor over a link and in the bottom left of the screen it will display the URL of the link, which is more than often an obvious sign as to whether the link is legitimate or not. You may even receive emails from coworkers or business acquaintances (or emails aliased to appear as if they are these users) with a link that looks questionable. You may want to give them a call or send an email directly using your email on file for them to make sure the link is legitimate.
In the end it’s always easier to double-check than to go through being victimized by ransomware.
Analyze sender email addresses carefully
Stemming from the previous point, make sure to analyze sender email addresses careful in any emails that may look suspicious. Sometimes malicious emails will have a domain that is almost unnoticeably similar to the legitimate company’s domain.
For example, a user might receive an email that seems like a great offer for an interest of theirs. The email may seem legitimate, but there is an embedded link that the email asks you to click on to retrieve an offer. If you hover over the link, it will display the URL of the link, which can usually be an obvious tell for the legitimacy of the link. Again: when in doubt, don’t click.
Backup your important files
One of the easiest ways to ensure that you always have access to your important files is to create backgups and keep them updated. Our partner company, Trend Micro, suggests employing the 3-2-1 rule for your important files:
Create 3 backup copies on 2 different media with 1 backup in a separate location.
Never use unknown/found devices
Have you recently cleaned out a closet in your home and found an old external harddrive, flashdrive, or even (let’s get real...) a CD that you burned a long time ago and wondered what was on it?
It’s fun to go through old tech in our home and travel back in time, especially with the surprise of plugging in a device that you might not have any idea what you put on it, and the excitement of seeing some old forgotten photos.
Don’t do that at work.
A less popular, but still available method of attack is to plant devices like harddrives and flash drives in offices or in public in hopes that someone will pick them up out of curiosity, plug them into their computer at work or at home and…
...now all of your information has been encrypted and you’re the victim of ransomware. Was that your tax information on your home computer? All of your photos of your High School Graduation? Or maybe it was all of that sensitive client information like social security numbers, account numbers, passwords etc. at work.
Yes, it’s extreme, but better to be aware of the worst-case scenario than to be the worst-case scenario.
Have a tested backup plan
NTS offers several different services related to Business Continuity to ensure that your data is not only backed up, but backed up securely and is easily and quickly restored in case of a disaster.
Update regularly
Last but certainly not least is to keep your software and systems up-to-date with the latest patches to make sure that any security flaws are being managed and repaired as soon as they are discovered.
The Social Engineering Test
I took a screenshot of a malicious email I had received on my work computer one day...
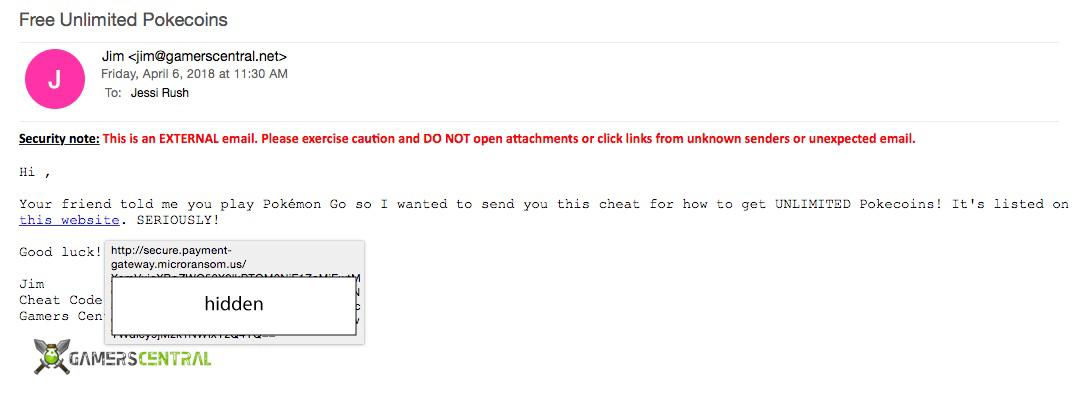
Unfortunately for this sender, I actually do not play Pokemon Go so I immediately knew that it was Spam. To the untrained eye this email may look like a legitimate-enough offer, the domain in the sender’s email address doesn’t throw up any red flags (jim[at]gamerscentral.net), it seems like a pretty great offer if you play this game, and the email is written comprehensively without errors, and they even provided a logo in the signature of the email.
But for the security-saavy, you’ll know to either ignore the email completely, or out of curiosity, hover over the link to display the URL of the link. You can see above in the grey box that the link would have taken me to secure.payment-gateway.microransom . us etc…
Seems like a pretty obvious giveaway, right?
Though I knew this wasn’t a legitimate email, I told one of my coworkers to come to my computer and look at how obvious the link was (to have a laugh) and it turns out that this was an email generated by one of our vendors, KnowBe4. KnowBe4 is “the world’s largest security awareness training and simulated phishing platform that helps you manage the ongoing problem of social engineering.”
 In this situation the punishment wouldn’t be a virus or ransomware, but something almost worse: the disappointment of bosses and coworkers who are all trained and certified in the ways of network security.
In this situation the punishment wouldn’t be a virus or ransomware, but something almost worse: the disappointment of bosses and coworkers who are all trained and certified in the ways of network security.
So as it turns out, this email was more or less a test of my “social engineering” to see if I was able to detect threatening emails and properly dispose of them, rather than clicking with caution to the wind.
